Activating HTTPS on IIS
After installation of the IIS web server and the esweb, it is necessary to activate the HTPPS protocol and bind the protocol to the esweb website.
es2000 does not make any recommendation regarding the suitability of the following information. Errors and exceptions are excluded and no responsibility is accepted for the information provided. The statements are simply descriptions and do not guarantee the consistency of the products. The information may also in part be regarded as an attempt to provide you with assistance for a task even if the product was not actually intended for this special purpose.
Operation of the esweb with an unsecured HTTP connection is not recommended for resons of security.
The HTTPS protocol is standard security technology that is used for the encrypted connection between a web server and a web client. HTTPS provides secure network communications by the identification and authentication of the server and by ensuring the protection and integrity of all the transmitted data. Because HTTPS prevents eavesdropping or manipulation of the information transmitted in the network, it should be used for every log in or authentication mechanism as well as for the entire network wherever communications contain confidential or proprietary information.
The use of HTTPS prevents spying on the names, passwords, and other confidential data that is transmitted between esweb / esmobile and the web server (IIS). When you use HTTPS, the connection to websites and resources is made using the HTTPS protocol instead of HTTP.
A server certificate bound to the website on which esweb is run is required in order to use HTTPS. Loading a certificate and binding it to a website will differ according to the web server.
You should also make sure that your web server is set up to ignore client certificates to ensure that access is via secure services using HTTPS.
Creating a server certificate
The web server requires a server certificate in order to make a HTTPS connection between esweb / esmobile and the the web server. A certificate is a digital file that contains information about the identity of the web server. It also contains the encryption technology that is used when a secure channel is set up between the web server and the esweb server.
A certificate is created by the owner of the website and signed digitally. There are three types of certificate: signed by the certification agency, domain-signed, and self-signed. These are explained below.
Certificates signed by the certification agency (CA)
Certificates signed by a certification agency (CA) should be used for productive systems, particularly if users outside your organization have access to the esweb server.
A certificate can be signed by an independent certification agency as well as by the website owner. A CA is normally a trustworthy third party provider who can confirm the authenticity of a website. If a website is trustworthy, the certification agency adds its own digital signature to the self-signed certificate. This guarantees to the web client that the identity of the website has been checked.
When a certificate that is signed by a recognized certification agency is used, secure communications between the server and the web client take place automaically without any special action on the part of the user. The web browser notices no unexpected behavior and no warnings are displayed because the website has been checked by the CA.
Domain certificates
If your server is behind a firewall and a CA signed certificate cannot be used, a domain certificate is an acceptable solution. A domain certificate is an internal certificate signed by the certification agency of an organization. The use of a domain certificate can reduce the costs associated with issuing certificates and simplifies the provision of certificates, as they can be quickly issued within the organization for trustworthy internal use.
Within your domain there will be no unexpected behavior or warning messages as would be the case with self-signed certificates, because the website has been checked by the domain certificate. Nevertheless, domain certificates are not checked by an external CA, which means that users accessing your website from outside your domain cannot check that the certificate is authentic. External users will see warning messages in their browser indicating that the website is not a trusted site, which may give the impression of communicating with a malicious attacker and may guide them away from your website.
In most cases you will receive the certificate from your IT administrator, who will bind it to HTTPS port 443.
Self-signed certificates
A certificate that is signed only by the website owner is called a self-signed certificate. Self-signed certificates are normally used in websites that are only available to users in the organization's internal network (LAN). If you communicate with a website outside your organization that uses a self signed certificate, there is no way that you can check that the website issuing the certificate is actually the website that it claims to be. You could actually be communicating with a malicious attacker, which would represent a risk to your data.
When self signed certificates are used, you can expect your browser to display warning messages indicating that the website is untrustworthy. When a web browser detects a self signed certificate, it usually displays a warning and asks you to confirm that you want to visit the website. Many browsers also display warning symbols or highlight the address line in red all the time that you are using a self signed certificate.
Creating a self signed certificate in IIS
Carry out the following steps in IIS Manager to create a self signed certificate:
-
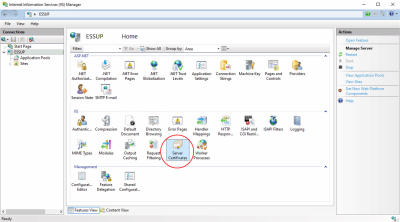
Start the Internet Information Services (IIS) Manager
-
Select your server in the structure view in the Connections area, and double click on Server certificates.
-
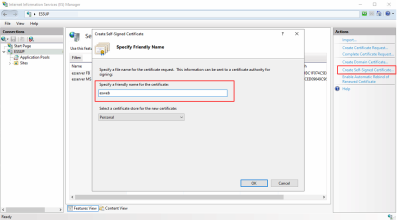
Click on Create self signed certificate in the Actions area.
-
Assign an appropriate name to the certificate and click on OK.
The final step is to bind the self signed certificate to HTTPS port 443. More information about this is found under Binding the certificate to the website.
Binding the certificate to the website
The certificate must be bound to the website on which esweb is running.
Binding is the process of configuring the certificate for the use of port 443 on the website.
The instructions for binding a certificate to the website differ according to the platform and web server version. More information about this can be obtained from your system administrator or the documentation for your web server. The steps for binding a certificate in IIS are given below as an example.
Binding a certificate to port 443 in IIS
Carry out the following steps in IIS Manager to bind a certificate to HTTPS port 443:
-
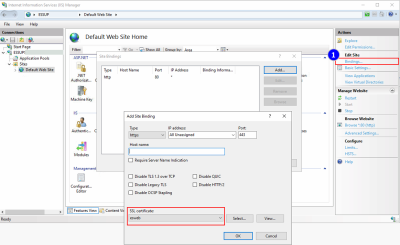
Select your site in the structure view and in the Actions area and click on Bindings (1).
-
If port 443 is unavailable in the list of bindings, click on the Add button. From the Type drop down list, select HTTPS. Leave the port set to 443.
Port 443 is the default port for HTTPS connecions. Other ports can be assigned by the administrator in line with individual security measures.
-
If port 443 is listed, select it from the list and click on the Edit button.
-
-
Select the name of the certificate from the drop down list of certificates and click on OK.
-
Remove the optional HTTP connection via port 80 (recommended!).
HTTPS connection test
You can now use https acces for esweb.
Please note that a connection is also possible only to the address for which the certificate was created.
A certificate for myserver.domain.local is not at the same time valid for https://localhost/esweb.
Self created certificates will generate a security warning indicating that the origin of the certificate cannot be checked when you open the website in a browser.